Essential Cybersecurity Tips for Remote Teams
Written by KRITIKA SINHA | MARKETING Your team is only one wrong click away from a major breach. A well-meaning employee opens a phishing email. A manager uses the same password across tools. Someone logs in through an unsecured Wi-Fi connection while ...
- All
- Awards30
- Cloud Services50
- Cyber Security171
- IT Consultancy39
- IT Procurement12
- Managed IT Services168
- Software Development42
- Sustainability9
- All
- Awards30
- Cloud Services50
- Cyber Security171
- IT Consultancy39
- IT Procurement12
- Managed IT Services168
- Software Development42
- Sustainability9
How To Reduce IT Downtime With Managed Services
Written by KRITIKA SINHA | MARKETING A single unexpected IT outage can bring even the most robust business operations to a grinding halt. Imagine a team unable ...
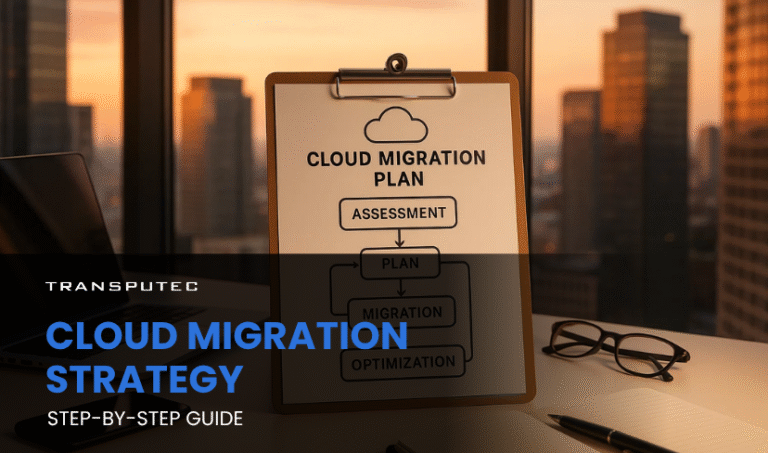
Step-by-Step Cloud Migration Strategy for Enterprises
Written by KRITIKA SINHA | MARKETING Departments stuck with slow, outdated systems. Employees juggling patchy remote access. IT managers buried under maintenance tasks rather than innovation. These ...
How Managed IT Services Help Businesses Fight Ransomware
Written by KRITIKA SINHA | MARKETING Business leaders know the feeling: you arrive at the office, log in, and suddenly your screen freezes. Files are locked, a ...
How To Choose A Secure Digital Locker For Your Business
Written by KRITIKA SINHA | MARKETING A single misplaced laptop can cost a business more than £30,000 in lost productivity, data breach fines, and reputational damage. Imagine ...
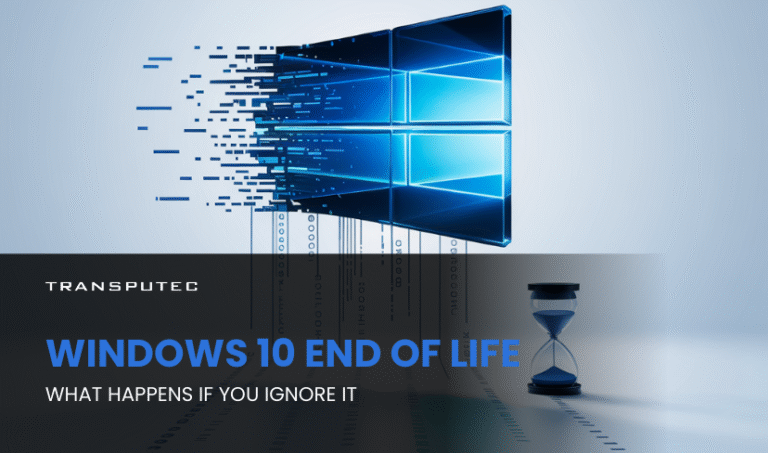
What Happens If You Ignore Windows 10 End of Life
Written by KRITIKA SINHA | MARKETING When your team’s laptops suddenly freeze mid-presentation or critical systems halt due to security breaches, your business doesn’t just lose time ...
AI For Business: Top 10 AI Tools For Business in 2025
Written by KRITIKA SINHA | MARKETING Are you feeling the relentless pressure of a rapidly evolving market, where traditional methods struggle to keep pace with escalating demands ...
10 Signs You Need to Upgrade Your IT Support
Written by KRITIKA SINHA | MARKETING “Why does my team spend more time fixing tech issues than serving clients?”“Are we losing business because our systems keep crashing?”“How ...
Managed Cyber Security Service: How Small Businesses Can Stay Safe
Written by KRITIKA SINHA | MARKETING A single phishing email, a forgotten software update, or an unnoticed network vulnerability—these are all it takes for a small business ...
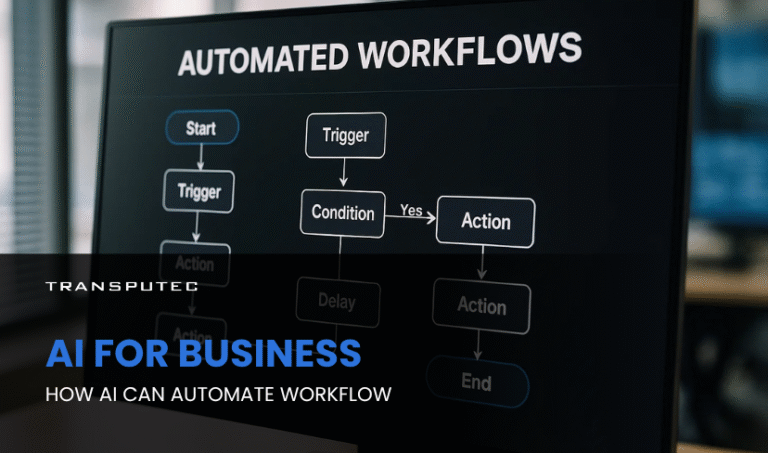
AI For Business: How AI Can Automate Workflow
Written by KRITIKA SINHA | MARKETING Picture this: your top sales executive spends more time updating CRM records than closing deals. Your finance team is drowning in ...
Co-Managed IT vs Fully Outsourced IT: Which One Is Right for You
Written by KRITIKA SINHA | MARKETING Technology issues can cripple business operations. IT downtime, cybersecurity threats, and lack of technical expertise often lead to financial losses, frustrated ...
Custom AI: How To Access AI That’s Tailored To Your Business
Written by KRITIKA SINHA | MARKETING Every business leader knows the frustration of wasted hours on repetitive tasks, missed opportunities buried in data, and the relentless pressure ...
How Business Automation Transforms Efficiency & Growth
Written by KRITIKA SINHA | MARKETING Your team spends hours every week on repetitive tasks: data entry, invoice chasing, endless spreadsheet updates. Deadlines get tighter, errors creep ...
Why SMEs Need SOC as a Service
Written by KRITIKA SINHA | MARKETING A small business is attacked every 39 seconds in the UK alone, yet most SMEs believe they’re too small to be ...
AI in Cybersecurity: How Intelligent Systems are Defending Against Advanced Threats
Written by KRITIKA SINHA | MARKETING Your firewall wasn’t fast enough. The malware had already breached your system before your IT team even had time to blink. ...
SOC 2 Compliance: What UK Businesses Need to Know
Written by KRITIKA SINHA | MARKETING Security breaches don’t just cost money—they destroy trust, disrupt business, and can even end careers. Imagine a single phishing email leading ...
Why Proactive Managed IT Services are Essential for UK SMEs
Written by KRITIKA SINHA | MARKETING Every business owner knows the feeling: the phone rings, and suddenly, your team is locked out of the system. Files are ...
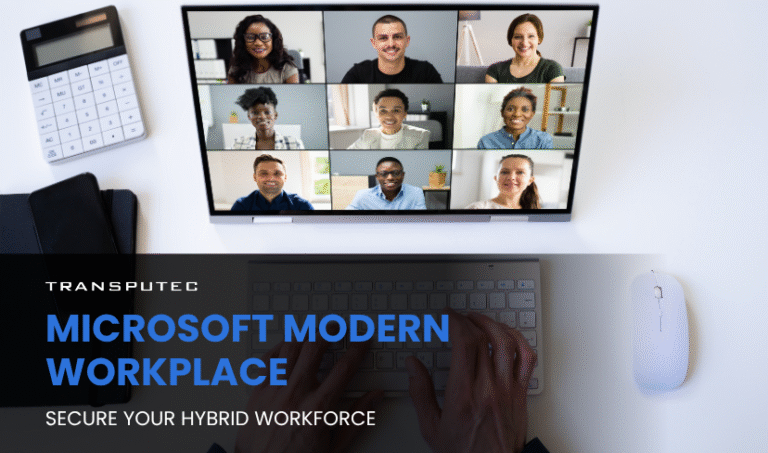
Secure Your Hybrid Workforce: How Microsoft Modern Workplace Protects Your Data
Written by KRITIKA SINHA | MARKETING Imagine this: a team scattered across time zones, working from airports, coffee shops, home offices—and your organisation’s most sensitive data travelling ...
How Microsoft Modern Workplace Supports SMEs
Written by KRITIKA SINHA | MARKETING Imagine a Monday morning where your team is scattered—some in the office, others at home, a few on-site with clients. Files ...
Everything You Need to Know About Microsoft Modern Workplace
Written by KRITIKA SINHA | MARKETING Do you often struggle with messy communication, separate bits of information, and a team finding it hard to work together in ...
10 Signs Your Business Needs Better Mac IT Support
Written by KRITIKA SINHA | MARKETING Tired of Recurring Mac Issues Slowing Down Your Team? Here’s What You’re Missing If your employees regularly complain about sluggish Macs, ...